2019-2020
ERSP Projects Heading link
In 2020-2021, we had a cohort of 28 scholars from the Computer Science and Electrical Engineering departments: 17 Computer Science students and 11 Electrical and Computer Engineering students. The ERSP scholars worked on a research project in teams of 3-4 students along with a faculty member and/or graduate student in the College of Engineering. Below you can find more information about their projects.
Dementia Detection Via Topic and Thought Process

Scholars: Noemi Andras, Jessica Borowy, Soyoon Lee, Ivana Pavlovic
Mentors: Dr. Natalie Parde
The Cookie-Theft Image will be considered as a “safe” zone that will determine when patients are wandering away from it in terms of their descriptions of the image. The goal is to understand the differences between thought processes of healthy and dementia diagnosed patients in order to apply this knowledge in future detection of dementia. In doing so, we hope to improve upon the accuracy of prior work in automated dementia detection. We expect to see that dementia patients engage in more ‘conversational wandering’ than healthy controls, sporadically jumping from one area of the image to another when describing it. This hypothesis is supported by psycholinguistic evidence suggesting that dementia patients tend to go off-topic and engage in verbal repetition when providing narratives. In future research, the new features would be evaluated using a logistic regression classification model. This model is what would be used to test if the developed features were accurately determining which patients had dementia and which were healthy. The model would sort patients into categories depending on the ‘path’ they took through the image with their descriptions and create a graph
Poster: Link to Google Drive.
#MeToo Twitter Data Analysis
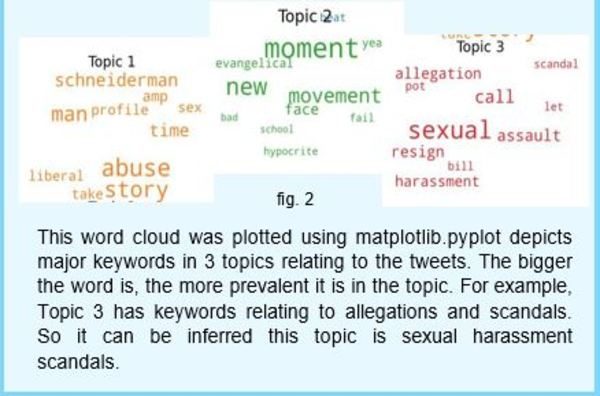
Scholars: Andres Tapia, Athalia Rochelle Handowo, Jeannine Gabe Tiemann
Mentors: Dr. Elena Zheleva (CS)
Our group analyzed the moral foundation (MF) frames in tweets and news articles referenced in tweets related to the #MeToo movement. We considered these MF frames when analyzing the tweets’ texts and the political leaning of the referenced news sources. From this data, we can begin to draw connections between traditional news sources and unguided Twitter user opinion.
Poster: Link to Google Drive.
Distributed Data Shuffling

Scholars: Sadhvi Kukreja, Krystian Tomczuk, Syeda Hussain
Mentors: Dr. Daniela Tuninetti (ECE)
Poster: Link to Google Drive.
Exploiting CRP Correlations in Arbiter PUFs
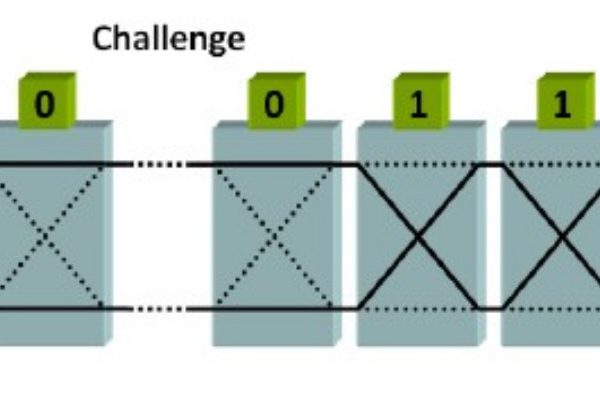
ERSP Scholars: Marius Zavistanavicius, Sasha Typkheeva, Eloisa Marquez
Mentors: Dr. Wenjing Rao (ECE)
PUFs are small circuits that can act as security primitives. It takes an input challenge and gives an output response, which is called a challenge response pair. PUFs can be used to secure client-server communications; the server would have a master list of challenge response pairs while the client would have the PUF.
To be secure, PUFs need to work like a black-box function that you can’t replicate. However, for years it has been repeatedly shown that PUFs can be modelled using machine learning. An attacker with physical access to the PUF can record challenge response pairs, feed it to a machine learning algorithm and create a model with 100% accuracy.
Our goal was to reduce the effectiveness of machine learning attacks by taking advantage of pairwise CRP correlations instead of creating a new PUF architecture.
Poster: Link to Google Drive.
Real-Time Fall Detection System
Scholars: Faraha Saadat, Akshat Kumar, Dua Shehadeh, Keziah O’Neal
Mentors: Dr. Cetin Enis Ahmet, Ouday Hanosh (ECE)
This research focuses on finding the optimum position of PIR sensors for real-time fall detection of seniors. Commonly used solutions for this problem include wearable technology, which are intrusive and require the subjects to wear the technology all the time. Our approach is through the optimum number and position of PIR sensors to detect if there was a fall or not. We investigate the use of low-cost, nonintrusive, contactless PIR sensors to record the movements caused by the fall, which then causes the motion sensors to output an oscillating signal. Through the analysis of the recorded data using deep learning algorithms, we are able to differentiate between regulatory movements and a fall. A statistical Infinite Impulse Response Algorithm is used to classify the data set of the motion sensors output into the occurrence of movement and no movements. Due to the COVID-19, we were unable to collect data for fall movements.
Poster: Link to Google Drive.
Investigating Radicalization in Twitter
Scholars: Srishti Pyasi, Jamie Rodica, Ameesha Saxena
Mentors: Dr. Chris Kanich, Dr. Taha Khan (CS)
Radicalization is defined as “the action or process of causing someone to adopt radical positions on political or social issues.” [1] The internet provides one of the greatest channels for influencing a great range of people via social networking websites like Twitter. Many violent/extreme acts taking place today are often a result of radicalization, which has caused lots of people to blame the internet. On social media, radicalization pathways typically follow a pipeline. The main purpose of our research is to determine the relationship between social media influence and the pathway leading to online radicalization.
Poster: Link to Google Drive.
Determining Urgency via Disaster Tweets
Scholars: Elijah Rodriguez Beltran, Arpita Kumari
Mentors: Dr. Cornelia Caragea (CS)
The issue is not solely the disasters themselves but the emergency response rate.Even after the main event of natural disaster,conditions such as floods, serve as immediate threats, and impede access to essentials such as food and water.In an emergency, the time between request and response can determine your survival.Therefore, it is imperative to search through large amounts of information and classify the urgency of a situation to aid responders’ efficiency and effectiveness in distributing resources or coming to aid.
Poster: Link to Google Drive.
Wearable Tongue-Computer Control Interface
Scholars: Maryam Ahmed, Mallika Patil, Mahal Schroeder, Anya Ellis
Mentors: Dr. Haneneh Esmailbeigi, Silvia Maddalena Rossi (BioE)
The design of the user interface app stands to benefit substantially from the adoption of key functionalities that increase the level of user-friendliness of the app and allow the user to better connect to the environment.
Poster: Link to Google Drive.